END-TO-END CYBERSECURITY SOLUTIONS
DHE can help you develop a roadmap to establish a proactive cyber security defense.
FEATURED CYBERSECURITY PARTNERS




CYBER THREATS ARE HERE TO STAY
Educational institution, governments, businesses large and small, and individuals around the world rely on interconnected digital technologies and systems for all aspects of their commerce, finance, and communications.
The challenge of securing personal information, intellectual property, and critical data has increased in parallel to our use of and dependence on technology. Motivated by politics, social activism, or greed, threat actors reach to every corner of the globe to intercept, exfiltrate, or disrupt the ever-increasing flow of data.
Identify and Manage Security Risks
- The required confidentiality, integrity, and availability of systems, applications, and information is determined and documented.
- Security risk management processes are embedded in risk management frameworks applicable to the organization and its mission.
- Security risks are to be identified, documented, managed and accepted both before systems and applications are authorized for use, and continuously throughout their operational life.

Implement Security Controls
- Systems are designed, deployed, and maintained according to their value. This value calculation should include the system’s confidentiality, integrity, and availability requirements.
- Systems must be delivered and supported by trusted suppliers and configured to reduce their attack surface.
- Systems and applications must be administered in a secure, accountable, and auditable manner.
- Security vulnerabilities in systems and applications are identified and mitigated promptly.

Respond and Recover from Cybersecurity Events
In today’s business environment, the likelihood of a cyberattack is relatively high. Being prepared to respond and recover is paramount. Policies around this capability should include:
- Cybersecurity incidents must be identified and reported both internally and externally to relevant bodies promptly.
- Cybersecurity incidents are to be contained, eradicated, and recovered from immediately.
- Business continuity and disaster recovery plans are to be enacted when required.
CYBER INCIDENT RESPONSE TIMELINE
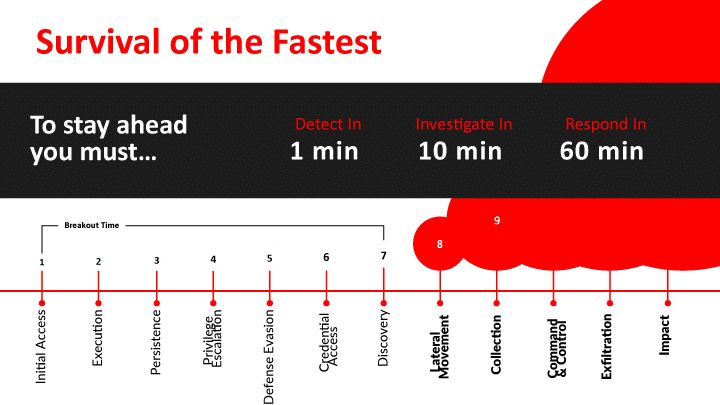
A fast and effective response is critical in stopping today’s breaches.
The first stages of an attack are the most critical when the adversary is:
- Establishing an initial footprint
- Achieving persistence
- And performing discovery
DHE CYBER SECURITY ASSESSMENT
DHE can help guide you through a high-impact process to develop your cybersecurity roadmap and implement a proactive cybersecurity defense system.

|
|
|
||||||||||||
